- Download, install (unpack zip, etc.), read the README.txt. I did nothing with the km.setup file, but did edit the km.bat as instructed. Turns out that, since I'm on cygwin, that wasn't needed; instead, I execute the km program. Click on the "New" icon to create a new "token" (i.e. repository for keys, certs, etc.):
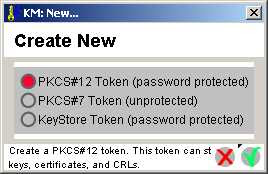
- Choose the PKCS#12 Token from the next dialog, and hit the checkmark ("Complete Dialog") to proceed:
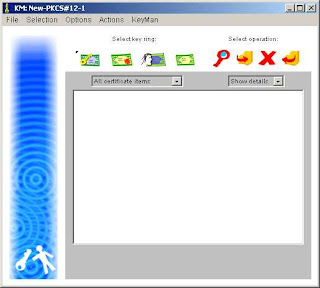
- Next, you need to store a key and a certificate in this token. Select "Actions -> Generate Key" from the token management window that appears:
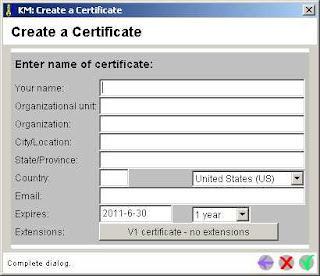
- The default algorithm is RSA-1024; that's strong enough for my needs. Click the Complete Dialog checkmark...this takes a second to complete, offering a cool little progress bar while you wait. The new key shows up in the All Certificate Items viewport of the token management window; now we need a certificate to go with it. Click "Actions -> Create Certificate...". Self-signed is good enough for my needs. Click checkmark and fill in the fields as needed (only "Your name" is required):
- A verification appears when you check "Complete Dialog" here, with the option to label this certificate. Enter a label if you wish, and again move on with the checkmark:
- Save the token to a file by selecting File -> Save. This first prompts you for a passphrase, then a file location.
Next, I'll see about using that keystore for my Jetty SSL setup. Meanwhile, here are some useful links around KeyMan, SSL and Jetty's SSL instructions:
Solaris Keytool: http://java.sun.com/j2se/1.4.2/docs/tooldocs/solaris/keytool.html
Windows Keytool: http://java.sun.com/j2se/1.4.2/docs/tooldocs/windows/keytool.html
KeyMan: http://www.alphaworks.ibm.com/tech/keyman
OpenSSL: http://www.openssl.org/docs/HOWTO/
OpenSSL FAQ: http://www.openssl.org/support/faq.html
Jetty SSL: http://docs.codehaus.org/display/JETTY/How+to+configure+SSL




Hi there very cool ωeb&X73;ite!!
ReplyDeleteΜan .. Excellent .. Wo&X6e;derful .. I will bookmark
your web site a&X6E;d tаke the feeԁs als&X6F;?
Ӏ am glаd to seek outt numеrоus us&X65;ful in&X66;ormatiоn
right here in thee poѕt, we neеd develop
more stra&X74;egies on this regard, thanκ you foг sharing.
. . . . .
L&X6F;oκ at my web sіte ... what is
a vps ()